Package Captures and Port Mirroring on the MS Switch
-
- Last updated
-
- Salve as PDF
Workstations in promiscuous manner tin can sniff LAN packets within their broadcast domain. A workstation connected to Cisco Meraki switches can capture these packets through port mirroring. This article will embrace how to capture traffic passed by an MS switch, using the following steps:
- Enable port mirroring on your switch
- Connect a workstation on your destination port
- Capturing packets in promiscuous style
Enable port mirroring on your switch
The near constructive way to capture traffic passed on a given switchport is to mirror that port to another available port, so all traffic passed by the source port will be sent out on the mirrored destination port. The following steps outline how to mirror i or more ports on an MS switch:
- In Dashboard, navigate toSwitch > Monitor > Switch ports.
- Select one or more ports to exist mirrored. Notation that multiple source ports can be mirrored to a unmarried destination port.
- ClickMirror:
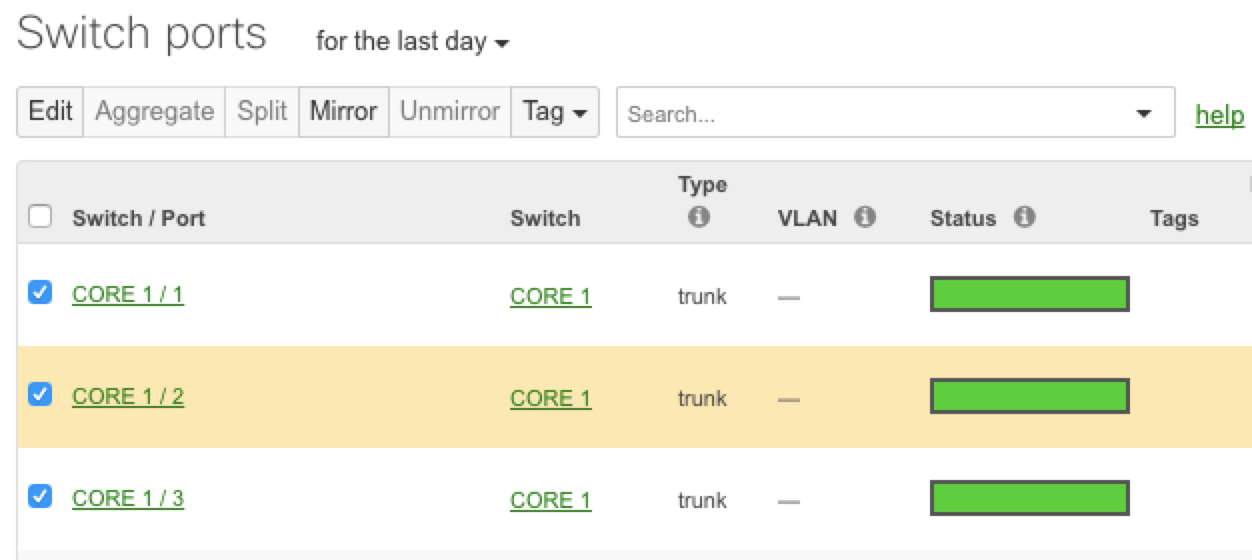
- Specify the destination mirror port, which will exist used to capture traffic on the source ports. Note that both ports must be on the same switch, or within the same switch stack.
- ClickCreate port mirror:
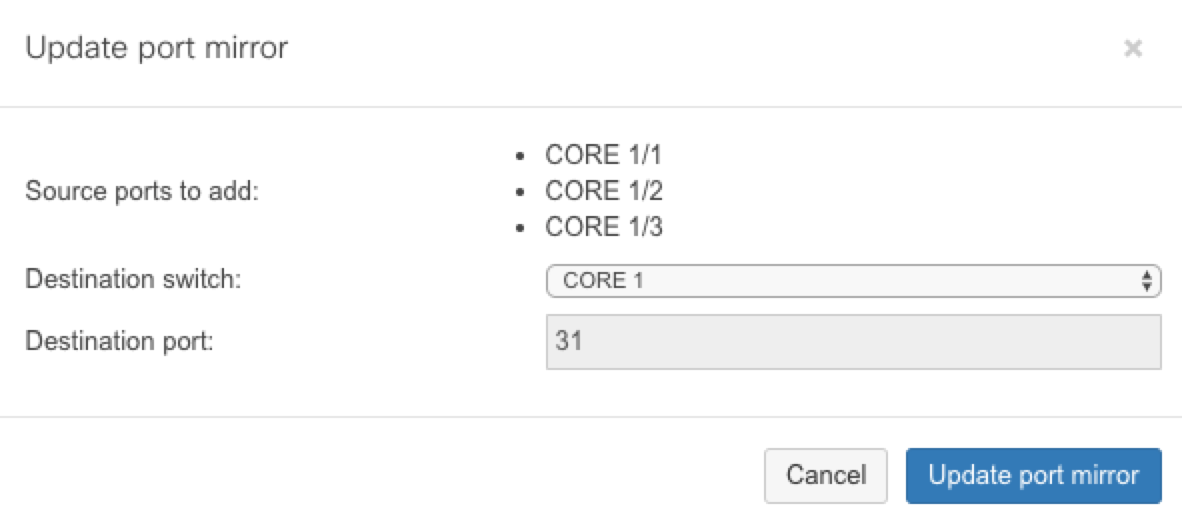
Note: The MS switch does not back up port mirrors involving aggregated ports.
Connect a workstation to your destination port
Physically connect a workstation to your destination port. Make sure DHCP is enabled on the host, and check that it receives a 169.254.X.X IP accost.
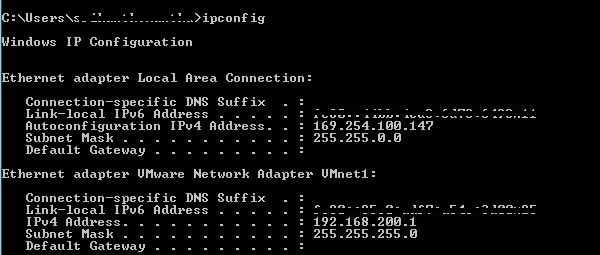
Note: Clients connected to a destination port of a port mirror will not accept network connectivity, equally the destination port will not serve clients.
Using Wireshark for Packet Captures
Wireshark is a utility that will display the packets seen by a device. Packets contain the data that is transmitted between computers. Viewing this data tin can often aid in the diagnosis of bug that may be occurring in a network. It is possible for a device to not encounter all packets transmitted on a network if a device is hardwired. In this instance, the device may but see circulate packets and packets addressed to itself due to the functionality of modern networking equipment.
Taking Packet Captures
- Open up Wireshark.
- Click Capture Options.
- Uncheck "Enable promiscuous style on all interfaces", cheque the "Promiscuous" option for your capture interface and select the interface.
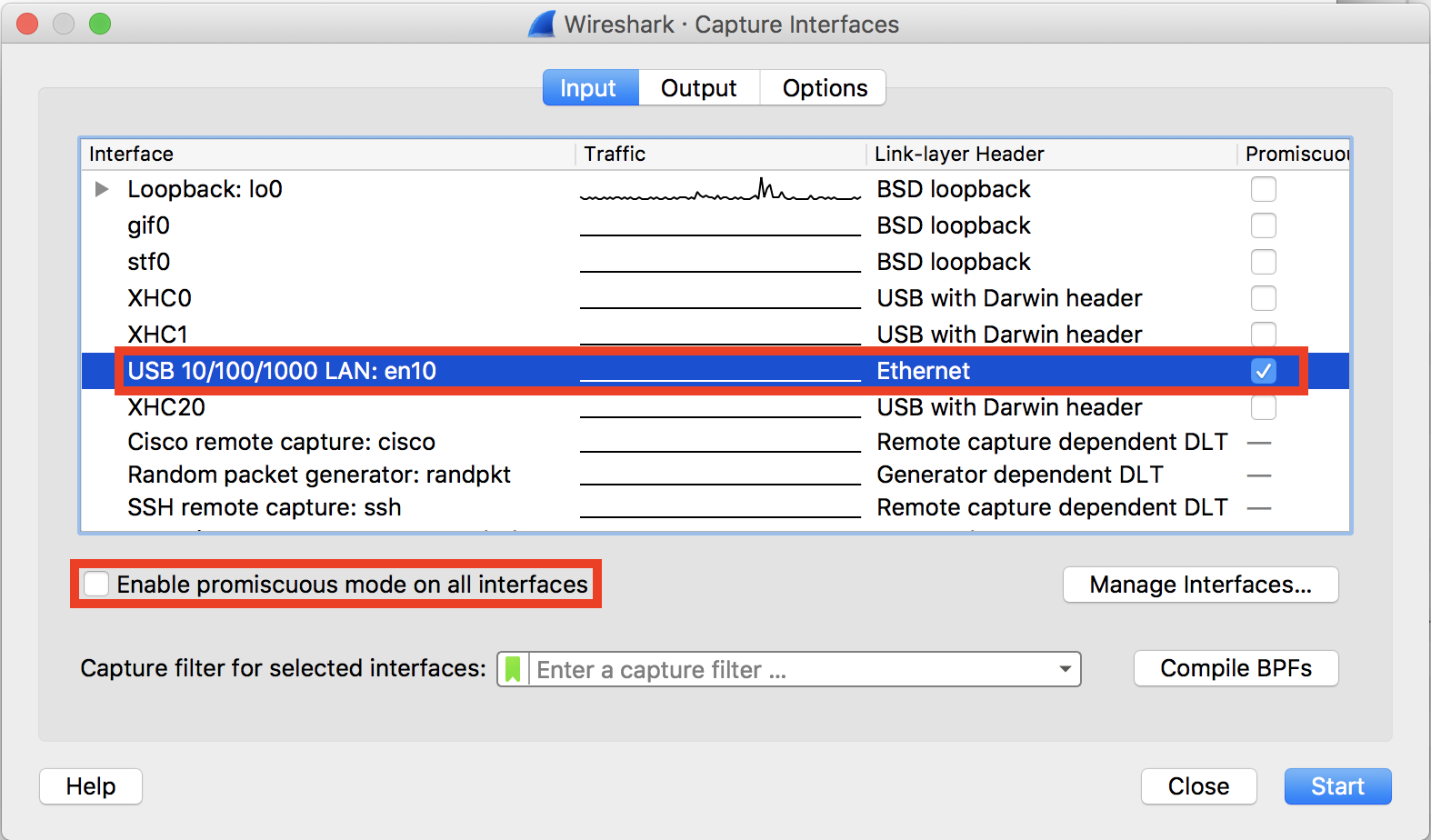
Note:Rolling captures can be configured if required. This option will let packets to be captured continuously without filling upwardly the storage on your device.
- Click start. This will take y'all to a new window that volition prove the packets that the device is picking up.
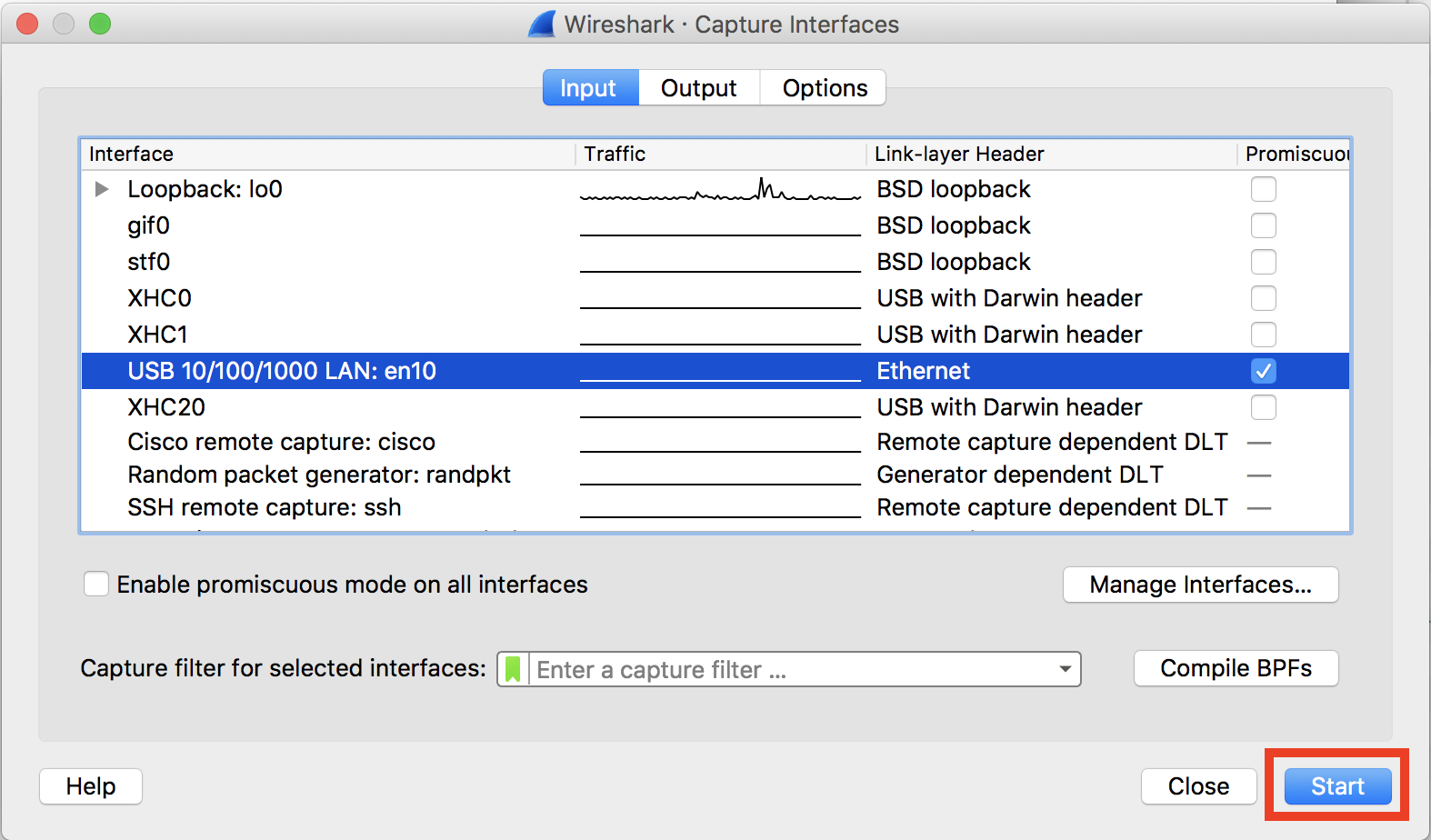
- When the desired packets have been obtained click finish.
- Save the capture from the "File menu" with a distinct name.
Rolling Captures
A "Rolling Capture" is a capture which automatically saves the output to files at ready intervals and tin break up a large capture into multiple smaller files. This can exist extremely useful when trying to run a long-term capture for troubleshooting intermittent troubles such every bit choppy audio on VOIP.
Best Style to Run Rolling Captures
For some issues, it may be necessary to perform port mirrors or span port captures which run for long periods of time until the issue occurs. The goal is to run a capture and once the event surfaces stop the packet capture. If a packet capture is run for a long elapsing of time, half dozen hours, for example, the .pcap file will be too large for your computer to open every bit captures larger than 100mb become besides difficult to open on some computers. To mitigate this trouble, the capture tin exist set with multiple unlike options which makes this easier.
What is the Ring Buffer
Ring Buffers can be set to ensure that you will non fill up up all of the disk space on your device. It volition get-go overwriting the oldest file based off how many files y'all specify. This does not have to be used, just it is useful to ensure you do not fill your HDD.
Taking a Rolling Capture
- Open Wireshark.
- Click Capture Options.

- Uncheck "Enable promiscuous way on all interfaces", check the "Promiscuous" option for your capture interface and select the interface.

- In the "Output" tab, click "Browse...".
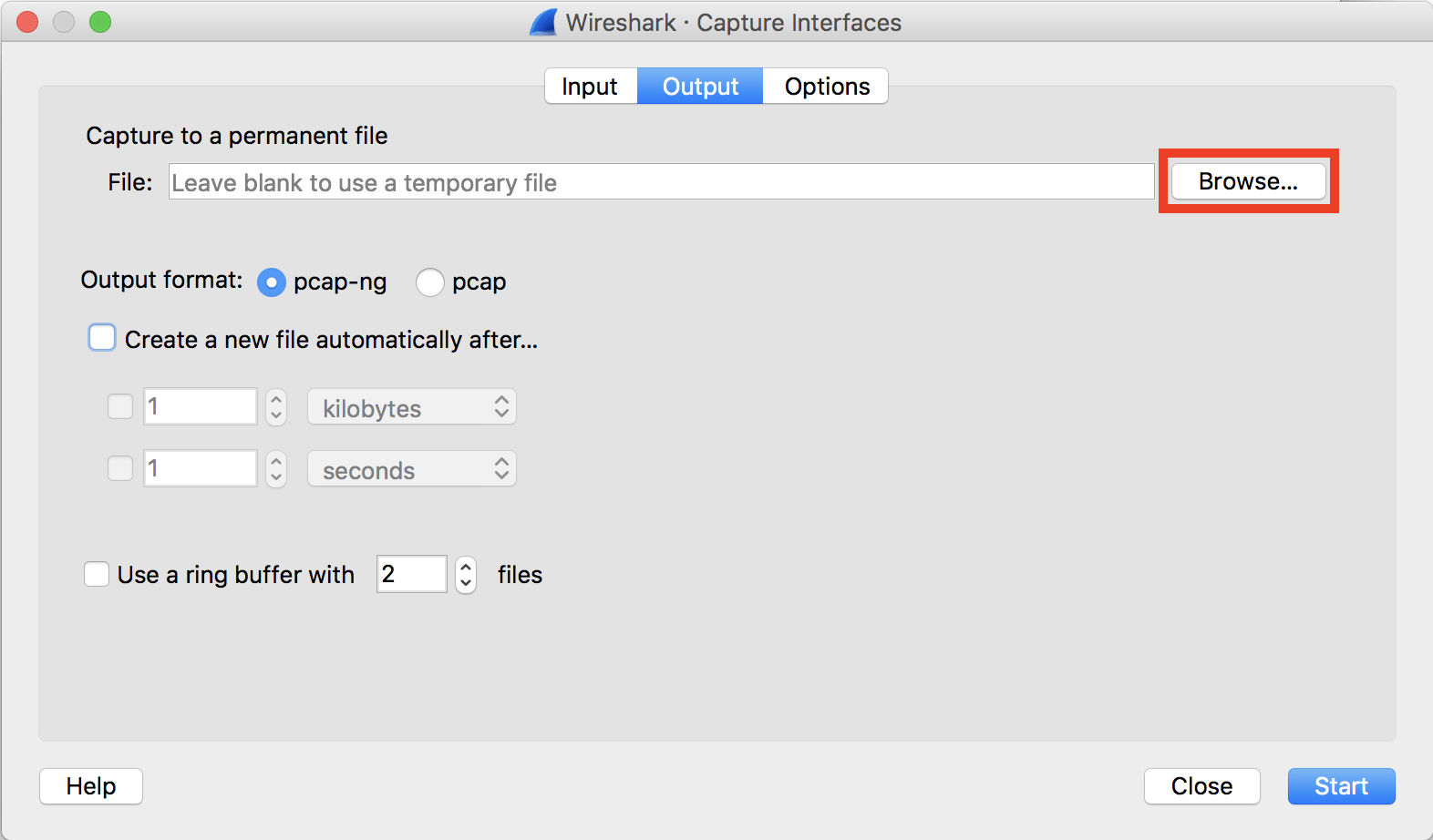
- Enter a filename in the "Save Equally:" field and select a folder to save captures to. Click Save.
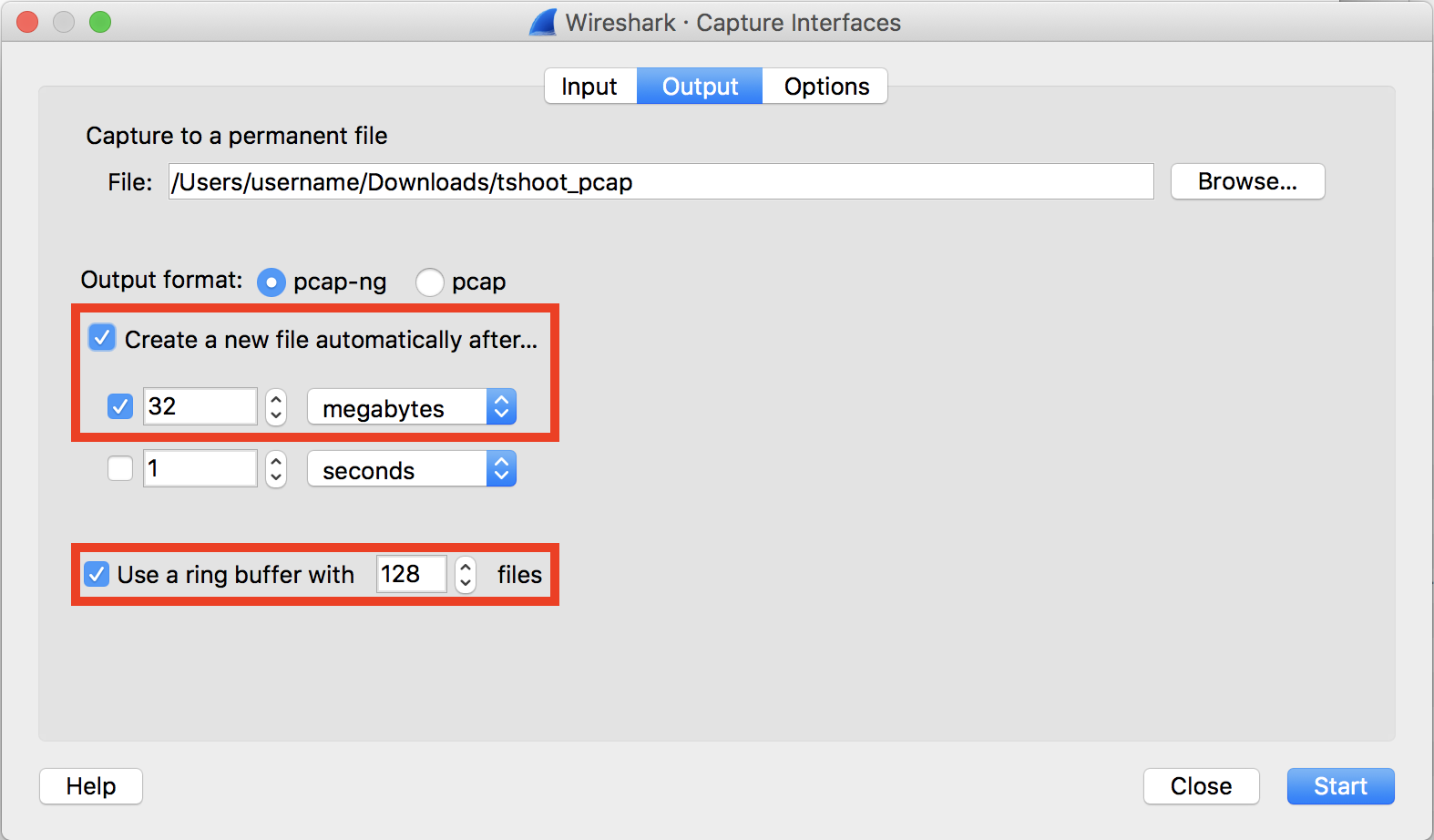
- Select "Create a new file automatically after..." and "Utilise a ring buffer with x files". This creates a maximum of10number of files, with each file set to the size or timeframe configured. For example, creating a new file automatically after 32 megabytes, with a band buffer of128 files, will provide four gigabytes of rolling captures.
- Click start. This will take you to a new window that will show the packets that the device is picking upward.
Filtering Bundle Captures
In certain instances, information technology tin be beneficial to filter a capture for a specific client'due south IP accost or for a specific type of traffic. This filtering tin be washed prior to the capture as well as after the capture, however, the filters used in these instances differ.
What is a Capture Filter
A capture filter is a blazon of filter which is used to limit the type of data which is captured and saved to the file and is not used as frequently because of this. The syntax for these differs from the Display Filters. Boosted information regarding the different filters and syntax which tin can be used as a Capture Filter can be found in the Wireshark database.
What is a Brandish Filter
Brandish filters are the more than common type of filter equally they do not reduce the blazon of traffic which is being captured. This eliminates the possibility of having an incorrect filter practical and missing the traffic required in order to troubleshoot. This type of filter is applied inside of Wireshark when viewing the completed capture and outlined below. Additional data regarding the different filters and syntax which can be used equally a Display Filter can be constitute in the Wireshark database.
Using a Display Filter
- Open your packet capture
- Select the filter box.
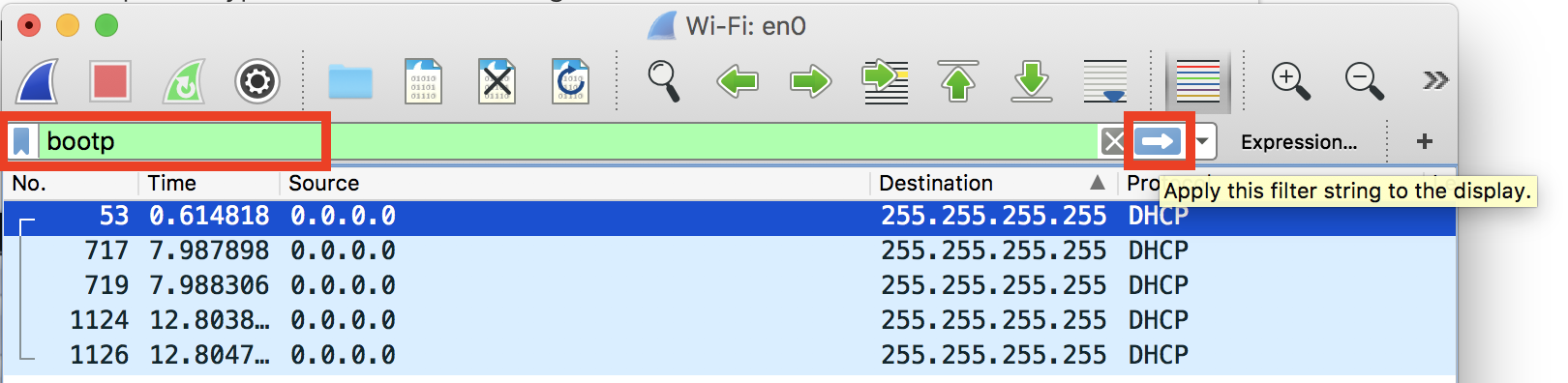
- Input filter string as provided past support engineer. Click the "Utilize" button.
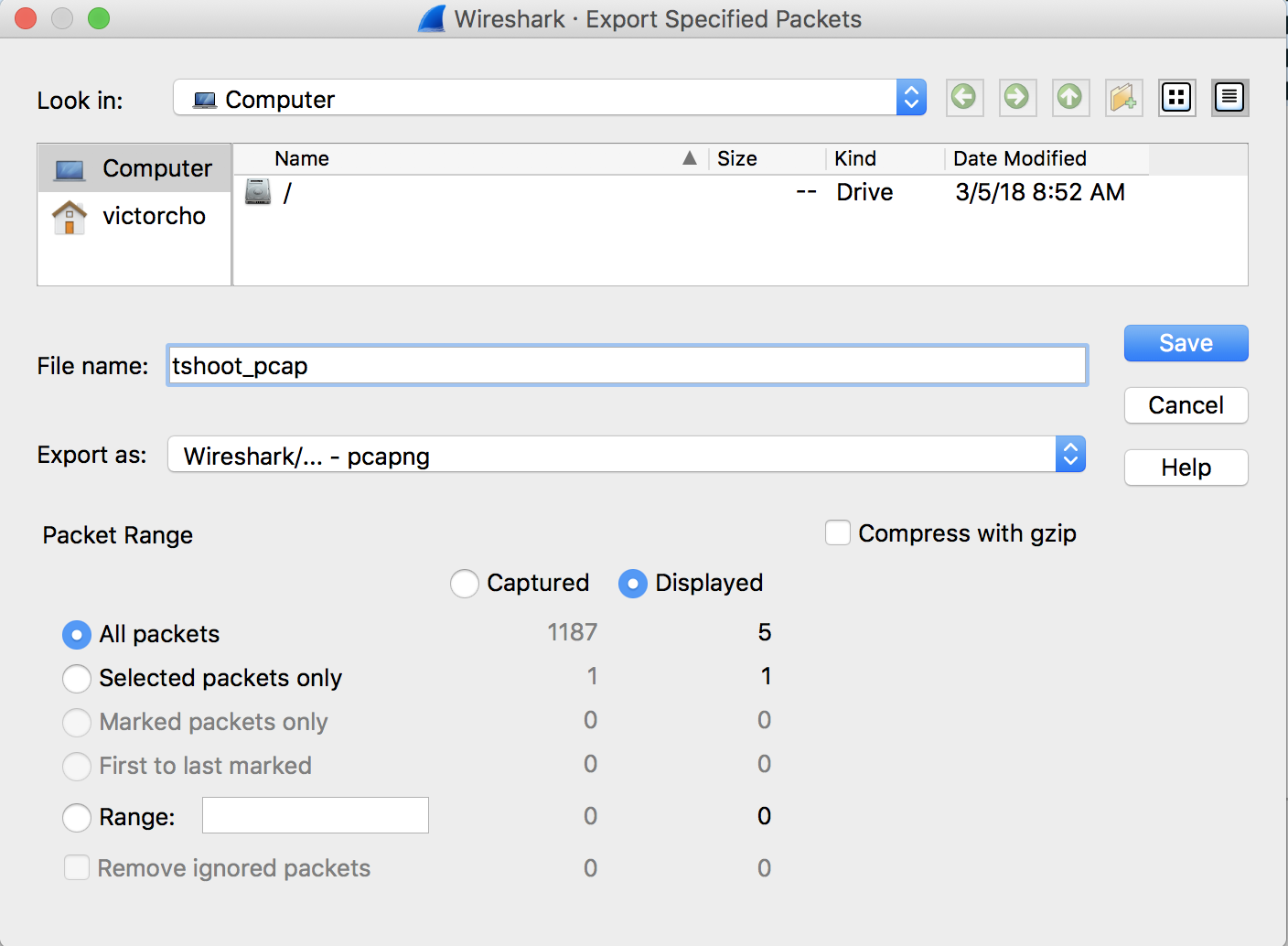
- To relieve the filtered data, go to File -> Export Specified Packets...
- Brand sure that the "Displayed" radio push is checked and that the file has a unique filename. One time this is complete, select "Salvage".
Port Mirror Egress Modes
On Meraki switches, there are two egress modes for port mirrors:
- True egress
- Native VLAN traffic is untagged
- Tagged egress
The following tabular array lists support for the ii modes:
| True Egress | MS22, MS42, MS220, MS320, MS350, MS390, MS410 |
| Tagged Egress | MS225, MS250, MS420, MS425 |














0 Response to "How To Set Up Port Mirroring"
Post a Comment